
SYEP 1
Screen shot of web page http://www.md5deep.souceforge.net/ from where we are gonna download md5deep hash generator.
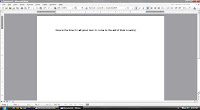
STEP 5
Word document created which shows" Now is the time for all good men to come to the aid of their country".

STEP 6
The above file is saved as country1.docx in the m5deep folder.

STEP 9
The HASH is 32 character long.

STEP 10
Below the Hash is created and it is also 32 character long same as country1.doc Hash length.

STEP 11
Opening Country1 document file.

STEP 12
Now the period is removed from the sentence and saved as country2.doc.
STEP 13
Length is same 32 characters long but the letters that are encrypted are completely different.
Length is same 32 characters long but the letters that are encrypted are completely different.
Using sha1 deep (SHA-1) the length of the country1.doc is 40 characters.

Now for country2.doc using sha1 deep length is same as country1.doc, but the characters are different.

Using whirlpooldeep hash generator the length of country1.doc is 128 characters.

Again, using whirlpooldeep hash generator the length of country2.doc is 128 characters but characters are different.
Cse Project 11.1 USES for Hashes.
Beside ATM's and passwords, what are other uses for hashes today? Use the Internet to explore how hashes are used in practical applications. Find three examples and write a one-paragraph description of each. Then, determine a way in which you would use a hash and write a description of it.
There are many purposes of hashes some of them are as follows.
1. Beside ATM's and passwords one of the important applications of Hashes is verification of message integrity, determining whether any changes have been made to a message or not which can be accomplished by comparing message degests calculated before and after transmission.
2. Hashes are also used to identify files on peer-to-peer file sharing network. For e.g. In an ed2k link and MD4- varient hash is combined with the file size, providing sufficient information for locating file sources, and downloading the file & verifying its contents.
Basically, I will use hash to check my important message/files integrity to know that it has not been tampered by an outsider or unauthorized person.
Reference
Cryptographic hash function.(nd) viewed on 30th jan 2010, retrived from
http://en.wikipedia.org/wiki/cryptographic hash function.
http://en.wikipedia.org/wiki/cryptographic hash function.


No comments:
Post a Comment